In a landmark development, Planet Zuda has successfully played an important role in Facebook amending crucial security issues, now allowing individuals 13+ with banned accounts to access and download some of their personal data. Our research indicates that, as per the California CCPA, all information should be available for download. As of our last assessment, Facebook has yet to allow full downloads of information for banned users.
This breakthrough is one of many direct results of a 3 month long campaign for Facebook to address the serious security breach in their moderation system, which allowed hackers the ability to ban accounts.
What was more intriguing is that these hackers worked in pairs, the one who would ultimately ban the account, hacked it first, and had control, potentially up to two months, before ever doing anything. They would log in every once in awhile, do nothing, and log out. This allowed them to learn where she was going, where she is usually, and where she was planning to be.
Based on what we know, they knew she was planning to go to a concert, so while our client was at the Taylor Swift ERAS concert in Los Angeles, the second hacker came on the scene, after she posted she was at the concert., tthat they knew she would be distracted for several hours, so when an alert came across her phone during the concert, asking if she just logged in, which she had, she pressed yes and went back to the concert.
Unbeknownst to any of the hacking, the second hacker had gained control of her account, which went through her account, changed the language and time zone and when the concert was about to end, they added the words copyright infringement to her last name, and than the first hacker took over and banned the account.
This lead to the ban to appear it was triggered by Facebooks AI, responding to the words copyright infringement in the name, which is in fact, a technique they used repeatedly as shown in this Reddit thread.
Facebook confirmed our findings that they were hacked, when we filed with their bug bounty program. Below are two screen shots of our communication with Facebook.
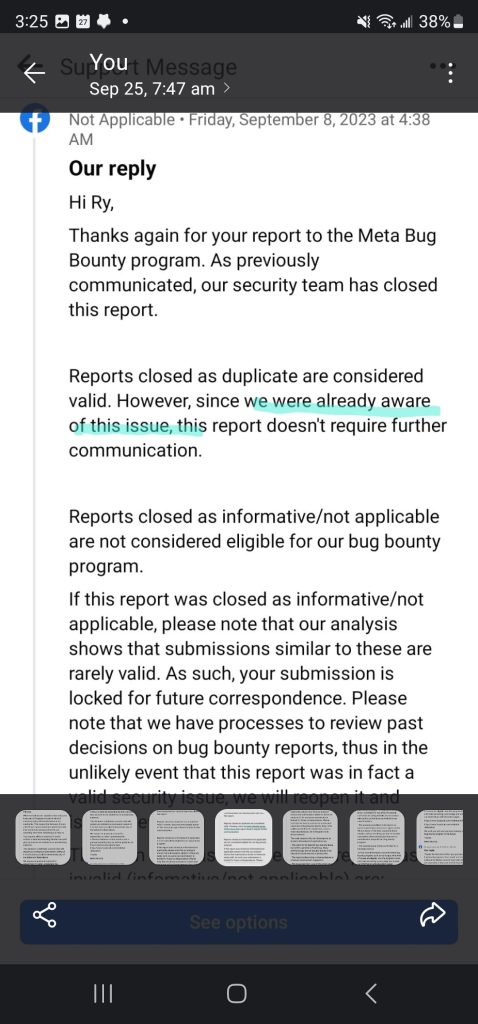
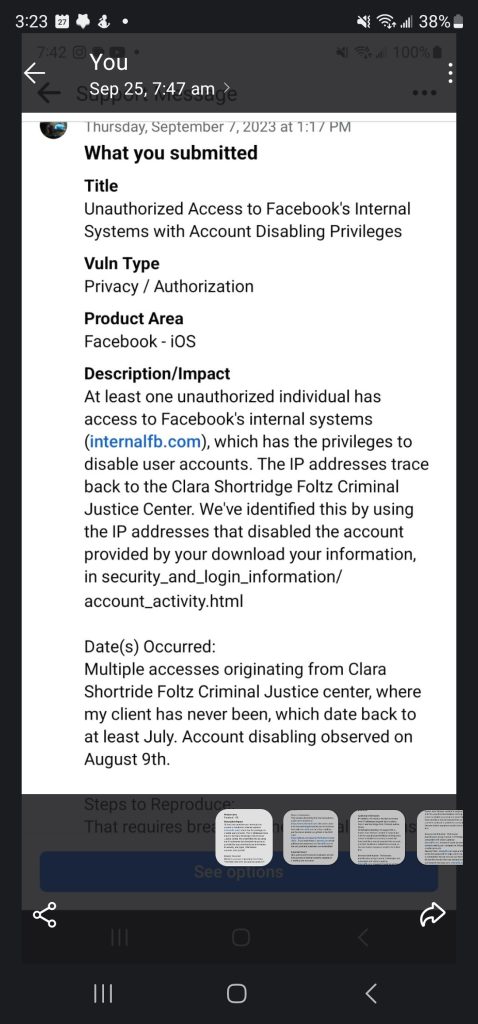
We unwaveringly communicated to Facebook’s legal representatives, which lead to the partial download of your information for banned accounts being added the next day after we contacted them. We also informed them of the breach in their clients systems multiple times. We than started a vigorous campaign that, while was initially focused on the restoration for our clients account, it evolved into trying to get all accounts banned by hackers reinstated, by spreading awareness of the issue to the FBI, FTC, the Department of Justice, and reporters.
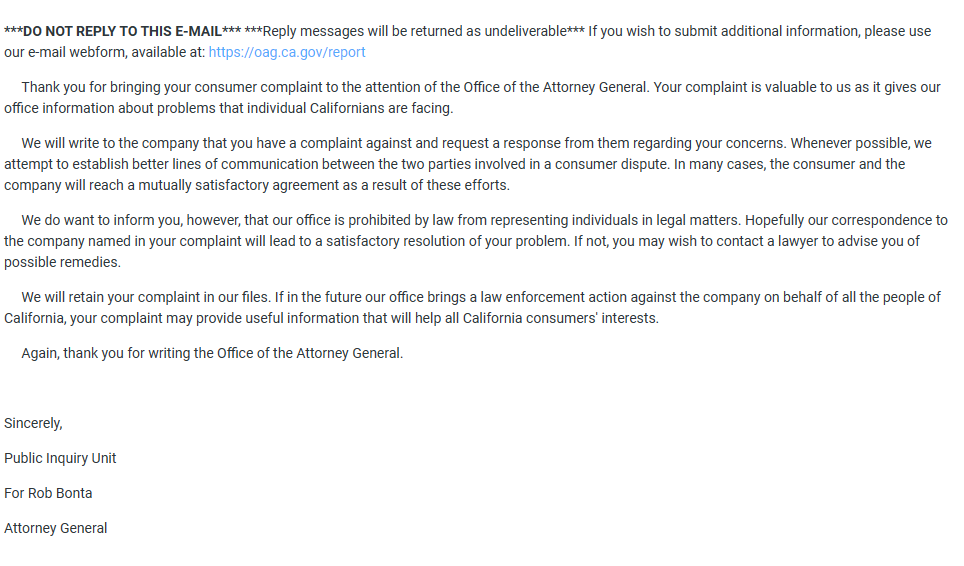
Our hundreds of hours of work, culminated in a significant victory on October 25th, when it was discovered that previously banned accounts were being reinstated en masse. These accounts changed from banned to locked, which now awaits verification from their legitimate owners email addresses and phone numbers that they provided prior to their accounts being hacked. In other words, Facebook reverted all the banned accounts by the hackers to their original unhacked state.
What is concerning for parents about the data breach, is that these hackers had moderator powers, presumably could’ve hacked teens accounts and now their communications might be for sale that criminals can buy. This intertwines with the Meta employees testifying that they weren’t protecting teens, and this data breach sends that message home, for teens and adults of all ages. If anyone under the age of 13 uses Facebook they also could’ve been compromised during this breach.
A positive result from this hack, is that they have now added additional security to the login sequence for Facebook moderators, now you have a code tied to your laptop, that you have to provide. It’s important to note that it still allows passwords, though it appears that iss being phased out, due to the breach.
While Facebook has yet to issue a formal disclosure of the breach or submit the hack to the California Attorney General Data Security breach system, When they submit confidential information of how the hack occurred is only visible to the Attorney General, but the fact that a breach has occurred, is available for all to see.
Conclusion: In an era where our digital footprints expand with each passing day, the importance of cybersecurity cannot be overstated. This incident with Facebook serves as a stark reminder of the vulnerabilities that exist, even within the platforms we consider most secure. It’s not just about protecting our online presence, but also about safeguarding our personal information, our memories, and in some cases, our personal safety. At Planet Zuda, our commitment goes beyond just identifying these vulnerabilities. We strive to ensure that digital platforms take responsibility, rectify breaches, and most importantly, prioritize the safety of their users.
Engage with Us: Have you or someone you know experienced similar cybersecurity concerns? We’d love to hear your stories and insights. Share your experiences in the comments below, or email us for help. By spreading awareness, we can collectively push for a safer digital future. If you found this information valuable, consider sharing this post on your social channels. Together, we can make a difference.



