Update: A new version of Paid memberships pro has been released to the WordPress repo, fixing the CSRF to stored XSS issue written about below, however anyone using paid memberships pro 1.9.2 or lower is still vulnerable. The sql injections still exist in many areas of the code, however some areas are protected, which we had yet to review. It does show improvement that two issues were fixed so quickly by the developer.
Paid Membership pro is a WordPress plugin that helps people buy your products and or services and is used on over 50 thousand sites, sadly the security is lacking. We were reviewing the plugin and discovered it is vulnerable to everything from sql injections and CSRF to stored XSS.While our information is usually locked down to paying customers, we decided it was in the best interest of the WordPress community to publicly expose these flaws. As always, Jetpack which is owned by Automattic reports this plugin as safe, due to the flawed way Jetpack decides if something is safe or not, which sadly gives users a false sense of security.
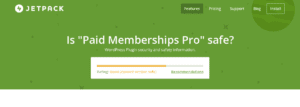
Incorrect security alert from Jetpack on Paid Memberships Pro
We reported Paid membership pro to WordPress security who removed the plugin from the WordPress repo. Unfortunately, removing a plugin from the WordPress repo does not help the affected users. Due to this problem, we believe public disclosure is best, especially since rewriting the plugin to fix all the issues in a timely manner would take a team of several people working solely on that project.
How is WordPress plugin Paid membership pro vulnerable to SQL injections?
This is a good question for those who aren’t used to security issues and the reason is simple. The developer either didn’t know about sql injection or didn’t know what to do about it. The code executes sql queries with little to no protection against sql injection. To put it simply, information that went into the database was not protected against criminals or researchers from manipulating data in the WordPress database, stealing all the data or doing whatever they like.
How is Paid Membership pro vulnerable to CSRF to stored XSS?
First it is important to explain that cross site request forgery, also known as CSRF and s XSS are two seperate security vulnerabilities tied together creating far more damage to the users site. CSRF allows a a researcher or criminal to copy a form or other code that needs CSRF protection to another website and then can trick a user to go to the site thus forcing them to unknowingly and unwittingly cause damage to their own website. In this case you had to be logged in as an admin who is tricked into clicking a damaging link. Again, in the case of the WordPress plugin Paid membership pro, the form in question is also vulnerable to stored XSS. Stored XSS, also known as stored cross site scripting allows a researcher or criminal to inject their own code into another website, whether that code causes damage or not is fully up to the attacker. In this case it caused defacement of the logged in admin panel and the site for users who are just visiting the site, which would’ve allowed the attacker to easily gain control of the entire WordPress site and cause damage to the users and the companies brand.
Here is an image of the stored XSS on Paid membership pro, where we simply made it show the number 1 to demonstrate that code could be ran. Any code, malicious or otherwise could’ve ran just for those who don’t understand that.

Where is WordPress plugin paid membership pro vulnerable to CSRF to stored XSS?
step 1: For csrf to stored xss login as admin and go to the admin panel.
Step 2: go to memberships and then click on add new membership level
step 3: There is no CSRF protection protecting this page, so it is vulnerable to CSRF.
Step 4: Go to parameter name and add in a simple ‘”><Script>
alert`1`</script> to get the vulnerability as seen above.
What should you do to protect yourself? At this point in time the only option is to switch plugins or have your team rewrite the code of the plugin, which is quite a task.
The best way to help protect other users is to share this article with others and alert them to this problem. If you want access to more WordPress security alerts and informative articles like this you will want to access our WordPress Plugin Security alerts. We will be doing write ups on plugins affecting over 200 thousand sites and another that affects 3 million sites for those who pay for access. We have yet to make our automated WordPress security plugin tool to automatically post to WordPress, so in the meantime we will provide updates for our customers often.