This ace app dating site social network review started in January, with one issue we asked them to fix. The issue was that all the users location, real name, and real pictures were being leaked. We originally thought this app only had 10 percent of all known asexuals, but thanks to aceapp social networks leak we discovered they had over 46 thousand asexuals of the 100 thousand that are publicly known by AVEN.
Aceapp acknowledged it as a feature publicly 6 months after contacting them when their competitor asexual.net wrote about it, so we released the below video of said feature.
We are now concerned that the owner claims an app with what appears to be an apparent sql injection is secure, yet also has many other issues that are just as bad when it comes to users safety, despite the last two updates saying they had privacy updates since the only privacy improvement was removing the feature of finding out users info. Originally the issue was only a 24 hour log of who was online last, where they lived and their real name and username along with their profile image. They then attempted to fix it, but instead made it worse by being able to expose everyone’s location, name and profile picture. We contacted them privately about making the issue they were claiming to be a feature worse, so they removed it.
Unfortunately for the LGBT+ community, you don’t need a feature or hack to see their private info, since aceapp still uses something insecure called http, which means your governments, your family, that weirdo in the coffee shop, they can see your messages and private information you’re sending on aceapp when using wifi. Using 4g or 3g will not fix the issue of your government being able to see it, and those who understand how to see 4g and 3g traffic. The way to fix this security issue will be changing to https.
aceapp announced they’re 100 percent secure in our comments and there wasn’t an issue, right after emailing us saying there was an issue. In the effort for transparency as a reporter we immediately published the email in full, typos from a mobile phone and all. The fact they say they’re is while knowing there appears to be a a sql injection that means it is a feature, not to mention the myriad of other security holes. We are leaving the majority of our updates intact to show you the painstaking hard work we have gone through and that we acknowledge it isn’t close to over.
Aceapp has around 50 thousand users according to their now closed feature. That is 50 percent of the known asexual community. A failure in their security affects us all and thus we must treat it and their handling of security as an attack on the safety of those who are asexual, as governments may look unfavorably at this, nonetheless we can not change who we are or how we identify as.
While our work to get them to stop telling the world when any user logged on is fixed and it took six months our work is far from over and this will continue to update to the public.
We also got them to make it so all the profile images can no longer be seen from the browser and downloaded via a browser scraper. Other avenues of attack may still exist. That’s the positive news, sadly.
One of the avenues of attack as we discussed above is http, which aceapp has replied demanding that was fixed in the June 4th update except for their terms and privacy page, sadly that isn’t accurate.
Googles chrome browser warns you when a site is not secure, even if they put https, and this is what you get when you go to aceapp.xyz
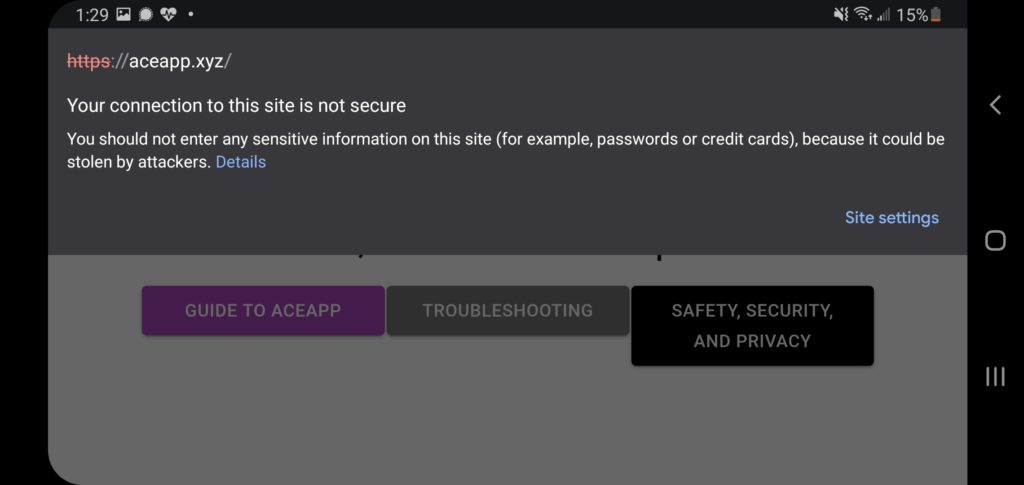
What is positive, is that they also claim they moved the images to a more secure system, we have not independently verified this and will be looking closely in to their claim.
If you accept those currently known issues as acceptable risks, we aren’t going to say not to use the social network, as we have warned you.
Now we are going to show you how aceapp looked recently, which they called a feature.
As we addressed above this was considered a feature publicly by them, which they publicly called a feature May 26th after asexual.net wrote about our research, so we released the above video titled feature or vulnerability? Along with their response
We were absolutely thrilled over a small victory on June 6th when the 24 hour log went to only a few people at a time, which looked like this.

Unfortunately, we discovered that this improvement had a new issue, we could now type in numbers to where it said id and cycle through 1 to over 100 thousand or until the database gave us everything in to the log. When we put in a random id which is simply a series of numbers, like 19968, it would then show that user, just logged in. If we did that to every user the log would display every user as logged in and disclose all their information.
Since it is pride month, we weote to them to report the issue, only to have them admit their was a problem, but then come and comment on here a few minutes later that there was never a problem.
Since we had been reporting on this we published the email correspondence for complete transparency. The below email exchange has only been fixed for typos.
Subject:Re: New exploit in aceapp unpublished
| From | ACEapp Help |
| To | ryan@planetzuda.com |
| Date | Today 02:27 |
Message Body
Hi Ryan, We truly appreciate your concern about the data breach on ACEapp. We want to inform you that all the data on ACEapp is completely safe and only authorized users can request and view the data. The only issue was with the getActiveNow where anyone can see data of all the online users at a particular time. We have fixed the issue already. Now no one can request any data outside the application without proper authorization.
Thanks. Let us know if you still find any such issue.
On Wed, Jun 10, 2020 at 11:07 AM <ryan@planetzuda.com> wrote:
Hello,
We tried contacting you before we went public with the 24 hour log of
users. Let’s put aside, what appears to be a sql injection and a way to
download all the users profile pictures among a few other public bugs.
In honor of pride month we are informing you of a worse issue you just
implemented, i hope was by accident. The getActiveNow.php file can now
expose not just a 24 hour l og we can download the entire database of every
users real name , username, location, state, country, province, city and
personal profile image.It is a simple bug to solve, you just provide a number 1,2,3, all the
way up to a million or until the database runs out of info. If we can
help with an issue that is getting worse, not better, then we need to team up.
.
Was I in the AceApp breach?
update 3/8/2020
.It is quite possible. Since at one point every user could be exposed, it’s possible they downloaded to every single image of every single user, username, name, and location that you provided.
What is asexual?
Asexual is part of LGBTQIA, and while this article previously said the A in LGBTQIA has dual meanings and while that is technically accurate, @asexuality the Twitter for asexuality.org, the leading information hub on asexuality says it erases asexuals. In light of this and someone who provided valuable feedback who goes by @dirtyunclekevin, we’ve amended this to reflect the community.
Asexual is a spectrum of people who have no interest in sex or romance to those who date through identity based relationships. Some have sex usually to please their partners, but if you want an extremely detailed guide go to asexual.org.
What have you done to protect users identities?
We did not publicly link to the API. We provided this information only to journalists who simply needed to verify the breach of users privacy, until aceapp deemed it a feature